Data Protection
Information Storage
Athento stores data in data centers across Europe (third-party datacenters). There is also an option to use the data center in Canada. All our european and mid-east asia clients are located in european data centers. Our US and Latin american customers may choose to be hosted in Europe or Canada.
Athento’s data centers provider follows strict measures of security and protection against other environmental elements.
Document and Database Storage
Documents and database information are stored in filesystem in servers. It is possible to encrypt the repository of documents at the request of the client.
Data Transfers with United States and UK
The documents of the clients of Athento Cloud, as well as the information on their documents (metadata) do not undergo any transfer to the mentioned countries. The data is stored on servers in France and/or Canada.
IMPORTANT
There will be data transfer to United States or UK if a user is placed in those countries and the user uses Athento.
The customer is responsible to have a Security Policy that controls what a user can or cannot do if the user is located in those countries and needs to access documents or information in Athento.
Identification and authentication
User identification and platform access control
The platform has a login system that requires of the introduction of a password and a valid user. Each user is identified unequivocally.
By default the user is authenticated in the platform by filling username and password in the login page. This information is compared to that stored in the database or transmitted by the configured identity provider. If the user name or password is invalid, a message is sent to the user.
Athento ECM uses authentication mechanisms based on JAAS (Java Authentication and Authorization Service) in a general way. Any request made to the platform must be authenticated, although public access channels may be offered for publication of anonymous documents or services.
Passwords managed in the system are encrypted if user management is done internally on the system or delegated to the user directory with which it supplies user or group information, for example, LDAP or ActiveDirectory, with all the Security applications included in them.
In addition, Athento ECM has the following possibilities for users and groups security management:
Integration with user directory systems such as LDAP and Microsoft Active Directory
Complete management of users and groups, both from the user directory and also from Athento’s own user/group directory. Allows the configuration of one or more user and / or group directories.
SSO Authentication and SAML2 authentication (compatible with cloud authentication systems such as Lastpass)
Possibility of integration with OAuth
The system supports integration with SSO, so that users can move between corporate applications without having to log in to the document manager, as well, this integration allows to transfer the permissions of the applications to the groups created in the document manager.
The flexibility of the system allows changing the method of authentication that comes by default with the application. The methods offered by the system in this sense are CAS (Central Authentication Service) -LDAP and Active Directory-, Portal Authentication, and Token Authentication.
Passwords
The platform makes use of user directories to control user authentication and password. For this, they are managed by default in an SQLBackend (database) where passwords are encrypted using the default SHA-256 encryption algorithm (also modifiable at declarative configuration time)
The user and the password must be kept confidential by the users of the platform. Users and Athento staff are responsible for protecting this information to prevent unauthorized access to the platform. Athento sends passwords by automatic methods that allow the passwords to be sent individually to the users.
If users forget their access data, Athento provides safe and reasonable methods for retrieving the data, the user is responsible for providing information for identification. In particular, Athento provides a form for password recovery via email. The user must enter the email or username in a form to request the automatic generation of a new password that will be sent via email.
Usernames and passwords can be assigned by several means:
The client company provides user names (emails or internal user codes in accordance with its identification policy) and initial passwords are assigned through an automatic process that generates random passwords for users. The access data is informed to the user individually and directly via email.
Admin users can create users from the administration center. By means of a form, the administrators can indicate the username and an email. The platform sends a link for users to activate their account and enter the password that they want to enter the system. In the following video you can see how this mechanism works. (https://vimeo.com/178399498)
Password Changes
The password change is done individually and automatically. From the user profile, the user can change their password.
You can also change it by clicking on "Forgot password". In this case, the user will receive an email with a link to change their password.
Password duration
By default and unless otherwise noted, passwords expire 12 months after they are introduced.
If the user tries to access with an expired password, the system will redirect it to the password change page.
Complexity of passwords
The password must meet at least the following characteristics:
Length: Minimum 8 characters
Characters to include: minimum two numeric digits, minimum one special character and at least two uppercase letters
Passwords already used
By default, a user password can not be reused for less than 720 days.
The system will inform the user of this circumstance.
Preventing unauthorized access
When a user continuously enters erroneous passwords for more than 5 times, the system prompts him to fill in a captcha. This prevents bots and malicious software from attempting to access the application by entering random passwords.
Access Log
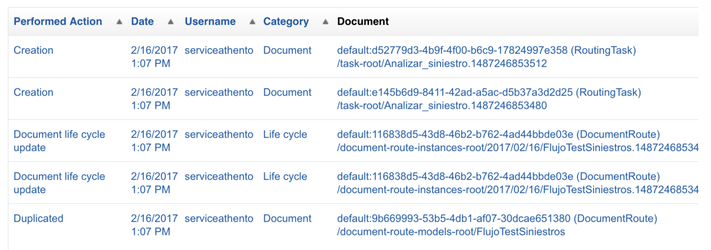
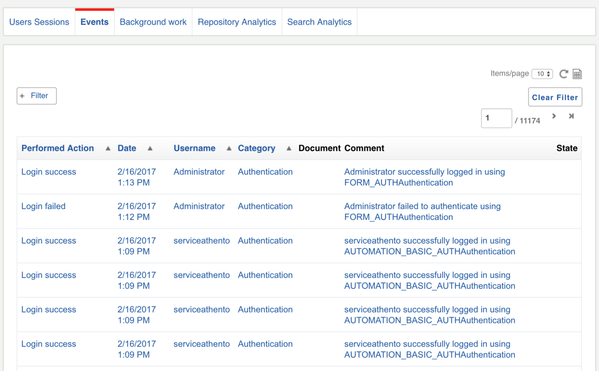
Athento allows you to generate reports detailing which user has accessed which document, information about the creation of documents or about their modification. We can filter by a range of dates or by user so that Athento allows to have at any moment information about the operations that each user performs.
The report stores the user ID, the date and time, the document that has been accessed, and so on.
Also, it is possible to know the user sessions in a certain time range to know who accesses the platform and denied access attempts to it.
Athento does not delete the previous audit trails.
Data Protection Issues
Record of Data Protection Incidents
Athento has a platform for recording the incidents of its customers.
Users can send their issues to the support mailbox or through the Support Center itself.
Our system of registration of incidents allows to store information on the reported incidence and exchange information for its prompt solution.
Some of the information that is stored for each incidence is:
Type of incidence
Time and date in which the incident is reported
User reporting incident
Person to whom the resolution of the incident is assigned
In addition, the system allows detailed documentation of the incident characteristics, measures to resolve it and, in general, any communication between Athento and the user reporting the incident. It is also possible to add users as a copy of the incident when it is considered that they should be aware of the situation.
If the solution of the problem involves data recovery, our team documents which member of our team performs data recovery, which data is restored and if any manual intervention has been necessary.